All you need to know about the DDEAuto exploit
You should be worried about the DDEAuto exploit, but more so about what’s coming next
One of the many ways hackers try to get their malware onto your computers, is by sending emails containing documents with macros. Most savvy users have enough knowledge by now to not activate macros in foreign documents.
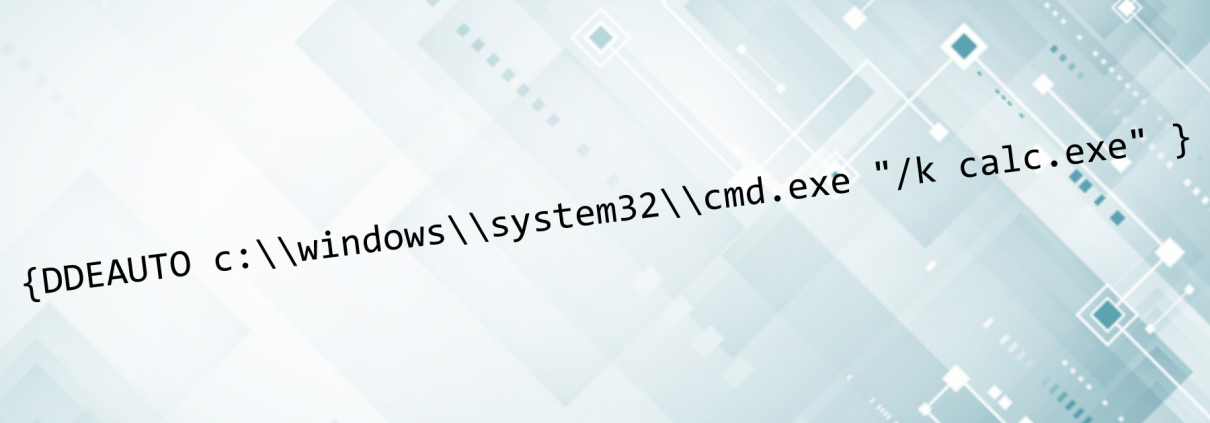
But recently, hackers have begun using the Dynamic Data Exchange (also known as DDE) feature, exploiting it to run commands on your computer. Originally, DDE is used to exchange data between different Microsoft programs, but attackers have now found a way of abusing it by adding a custom field inside a document, instructing it to launch malicious code.
The problem exists in all of your Microsoft Office applications. That’s Word, Excel, Access but also inside an email you’re reading, or a calendar invite.
On the good side, users are currently receiving a warning which informs them of the given file containing DDE links, which may direct to different documents. But the warning is new to most users, possibly tricking them into pressing “Yes” instead of “No”.
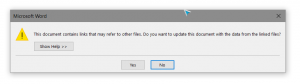
Since the DDE feature is not considered suspicious, traditional anti-virus doesn’t block files with DDE fields. Like macros, the feature can be both good and bad, depending on who crafted the document.
Should you say “Yes” to the above, you get another warning:
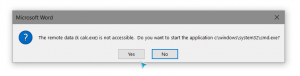
Another “Yes” will possibly land you in a world of trouble. (Above screenshot is of a benign calc.exe test command-line, so that’s just “popping calc”). Threats in the wild are already obfuscating the command-line to make it look innocent.
What should you do?
Basically, just say no.
But to mitigate this exploit entirely, you can disable the DDEAuto feature completely. There’s a good chance you never need it.
If you want to do this automatically, there’s a .reg file on GitHub that fixes this for several versions of Microsoft Office:
https://gist.github.com/wdormann/732bb88d9b5dd5a66c9f1e1498f31a1b
Always remember
- Consider external files or links sent to you carefully
- Take warning pop-ups seriously, even though they are new to you
But the worst problem still remains …
Albeit the current warning window raises the red flag, what if in the future attackers don’t even need that confirmation in the form of simple “Yes” or “No”? That is the real nightmare threat.
And this is exactly why we created SectionGuard.