Reaching Domain Admin and beyond
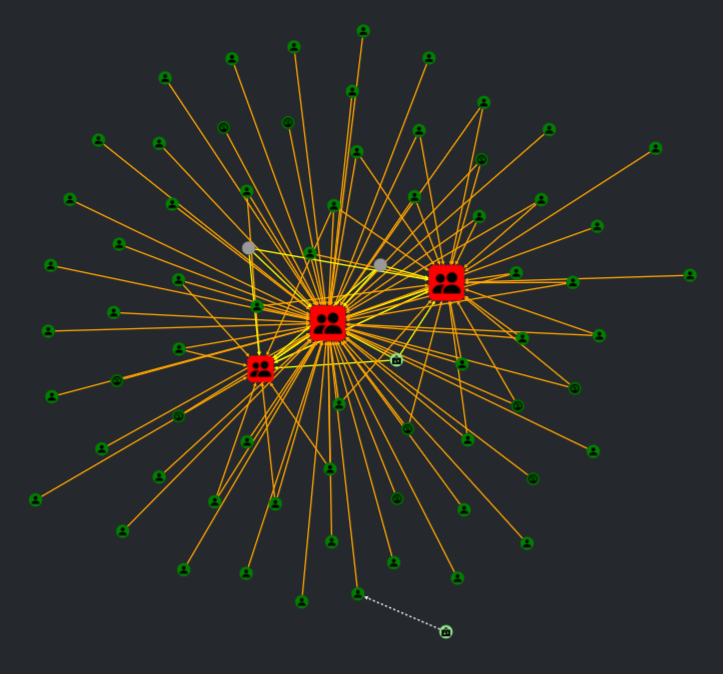
The most popular search (and the one Adalanche defaults to when you launch it, is the “Who are or can become Domain Admin”. The graph shows you call users, groups or machines that can end up taking over your entire Active Directory infrastructure.
This is not all there is to it though, there are numerous ways to take over an Active Directory, and different searches tells different stories. There are more than 10 predefined searches, and lots of options to narrow down results.
Problems range from DCsync attacks, certificate templates, bad usage patterns etc. Adalanche has you covered, simply ask for a scenario, and you get instant answers if the data is available to Adalanche.
Supply chain attack analysis
After multiple breaches happening due to supply chain attacks – the most well known being the Solarwinds breach – it’s due time to look at risks this poses to your infrastructure.
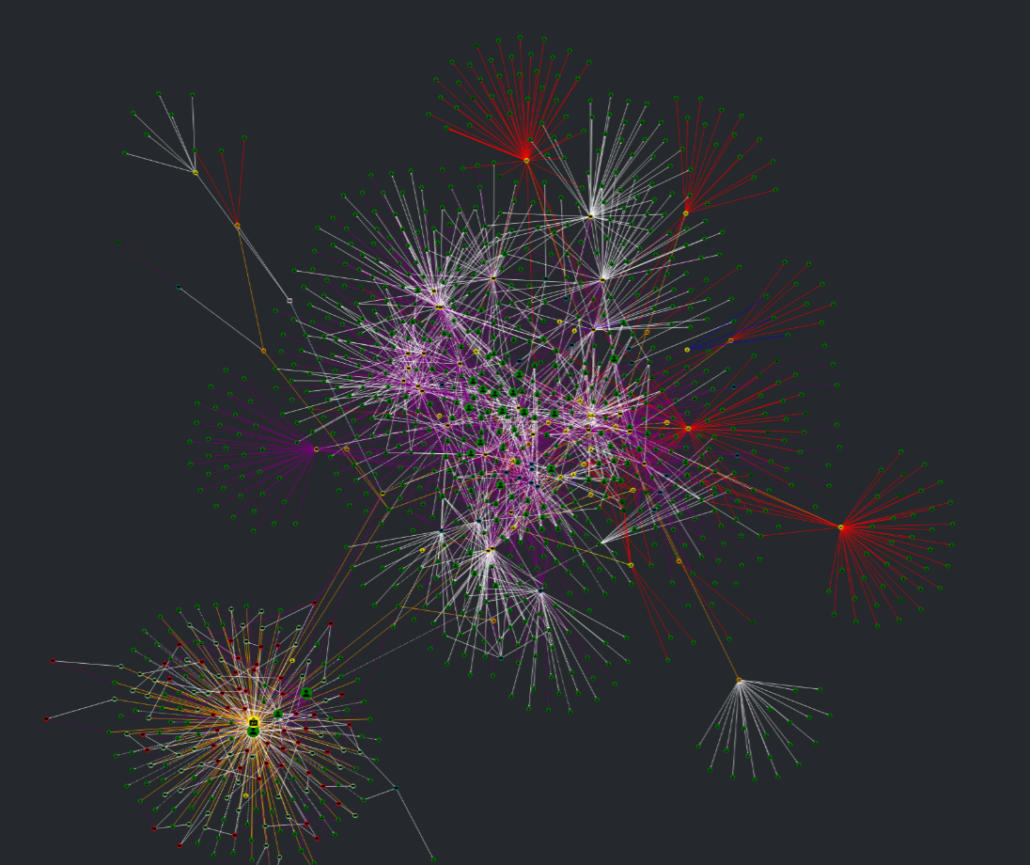
When Adalanche is augmented with data from local machines, it is possible to do a search based on installed software. This can give you the answer to what gets impacted if a particular piece of software gets compromised from an update or a vulnerability.
Searches and be done on any kind of knowledge that Adalanche has in the graph, ranging from operating system versions, installed software or knowledge points you import via custom data in the Professional edition.
Sample graph showing machines with Steam gaming platform installed, and what impact that can have on your infrastructure components
Certificate Template Security
Letting users enroll into dangerous published Certificate Templates can be a way to grant them a way to pose as any user in Active Directory, and is a very common mis-configuration we find. Write permissions on Certificate Templates can weaponize any Certificate Template that lets attackers become anyone they want. You can let adalanche do the heavy lifting on analyzing these paths.
Tiering model validation
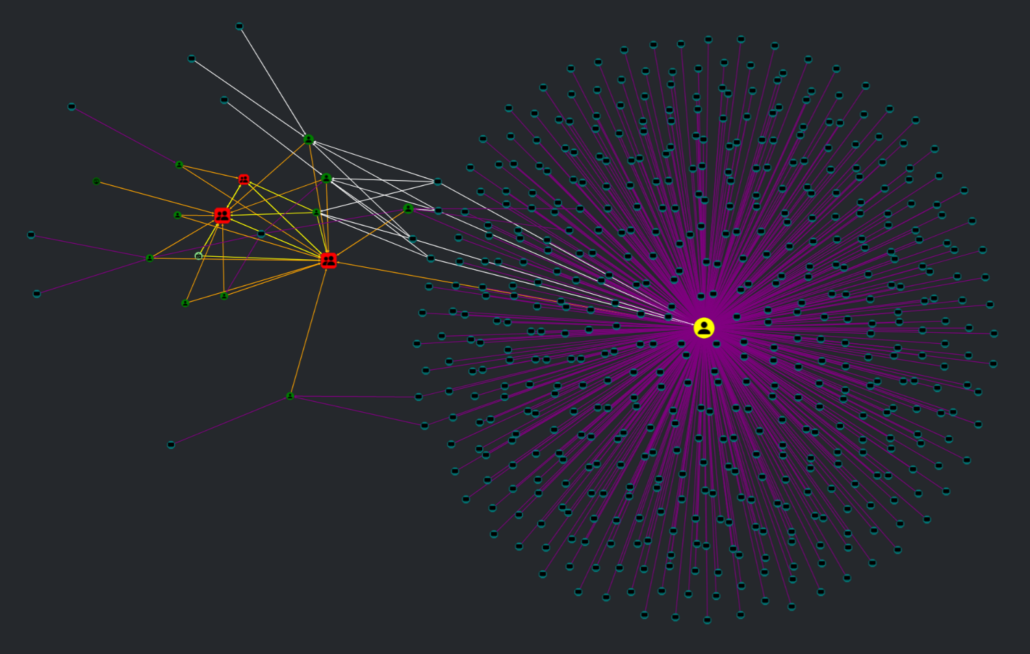
With cross control plane tiering validation, you can ensure that you’ve got your tiering set up correctly.
You can define an unliminted number of tiers and combine this with the possibility for parallel tiers. Check that terminal server admins or DBAs can’t admin other servers, by assigning them to a tier, and let Adalanche do the rest!
It doesn’t matter if the tiering violation is in Active Directory, in VCenter or in CyberArk – if it’s defined in the model, you can validate it. Every tiering violation will show up in the graph for visual inspection, making remediation both easy and possible. As a tiering violation is a regular edge, you can export data pairs as well, and postprocess as you need.
Sample graph showing how a tier 0 account is logging in to a wide range of machines, making an attack possible from every machine by grabbing NTLM credentials